- Products
- Email Verifier Verify emails addresses individually, in bulk or through API, with 99% accuracy
- Email Finder Find individual or bulk emails by entering the person & company name or domain
-
Form Guard Protect your forms from spam, bots, and invalid submissions with real-time email, phone, and name verification.
- Prospect SQL/MQL list building with high levels of personalization, real-time data enrichment and prospect search
- Clearout For SheetsVerify email addresses directly on Google Sheets with Clearout for sheets add-on
- Prospect – LinkedIn Chrome ExtensionBuild verified, targeted prospect lists directly from LinkedIn profiles
- ClearoutPhoneValidate phone numbers across 240+ countries in bulk, quick or real time validation Free Tools
- Disposable Email Checker
- Reverse LinkedIn Profile Lookup Tool
- Reverse Email Lookup Tool
- Email List Cleaner
- ResourcesDEVELOPER
API
Clearout APIs are structured around REST and JSONWebhooks
Capture real-time events in your application workflowForm Guard
Real-time form validation to keep bad contacts out of your CRMKNOWLEDGE BASEGetting started
Sending campaigns without bounces is made simpleFAQ
Easily find answers to services, security and common questionsUSE CASESLead Generation
Learn how professionals generate quality leadsGUIDESPricingTransparent & flexible pricing to support pay-per-use or recurringCompare Email Verification Tools
AI-powered email verification with 99%+ accuracy, real-time validation, and transparent risk scoringCompare Email Finder Tools
Pre-verified B2B email addresses with confidence scoring, find real person email, not role-based addressBLOGSEmail Verification ToolsFind Anyone’s Email Address
Most Accurate, Fast & Free WaysForm Validation
Importance, Ways & Best PracticesView All Blogs - Pricing
- Integrations
- Enterprise
- Login
Email Security Best Practices Every Email Marketer Should Know

Introduction: Emphasizing Email Security in Marketing Campaigns
However, the growing reliance on email also makes it an increasingly attractive attack vector for cybercriminals. Verizon’s 2021 Data Breach Investigations Report found email to be involved in nearly 1 out of 3 data breaches. High-profile attacks like the SolarWinds breach impacted over 18,000 organizations and highlighted how compromised email accounts can enable broad network infiltration and espionage capabilities.
For marketers, a breach of your email environment can enable cybercriminals to distribute malware, launch phishing scams on your customers, and misuse your brand identity for nefarious purposes. This is why, among other things, email list hygiene is crucial. The impacts of such breaches can range from temporary deliverability issues to permanent reputational damage, legal liabilities, and loss of customer trust. By prioritizing robust security protocols, and secure email providers, marketers can continue harnessing the power of email while safeguarding the interests of customers and their brands.
The Growing Sophistication of Email Threats

- Phishing attacks increased by 220% during the pandemic according to a Google report, exemplifying how crisis events exacerbate security vulnerabilities.
- The FBI reveals that business email compromise scams have cost organizations $43 billion since 2016, with a sharp upward trend.
- Between 2020 to 2021, ransomware attacks increased by 105% according to SonicWall, with email being a primary infection vector.
- Security firm Barracuda Networks found that more than 1 in 5 organizations have suffered email account takeovers, enabling wider network infiltration.
- Agari's research found that 84% of organizations feel vulnerable to domain spoofing attacks that can enable brand impersonation through fraudulent emails.
Deep Dive into Key Email Threat Types

Phishing Attacks
To further enhance your defense against phishing attacks, consider using a VPN. You might be wondering, "Should I use a VPN?' The answer is Yes, a VPN can add a layer of protection by encrypting your internet connection and masking your IP address, making it harder for cybercriminals to trace your online activities and increasing your overall security.
Malware Infections
Account Takeovers
Insecure Data Handling
Business Email Compromise
Implementing Core Email Security Best Practices
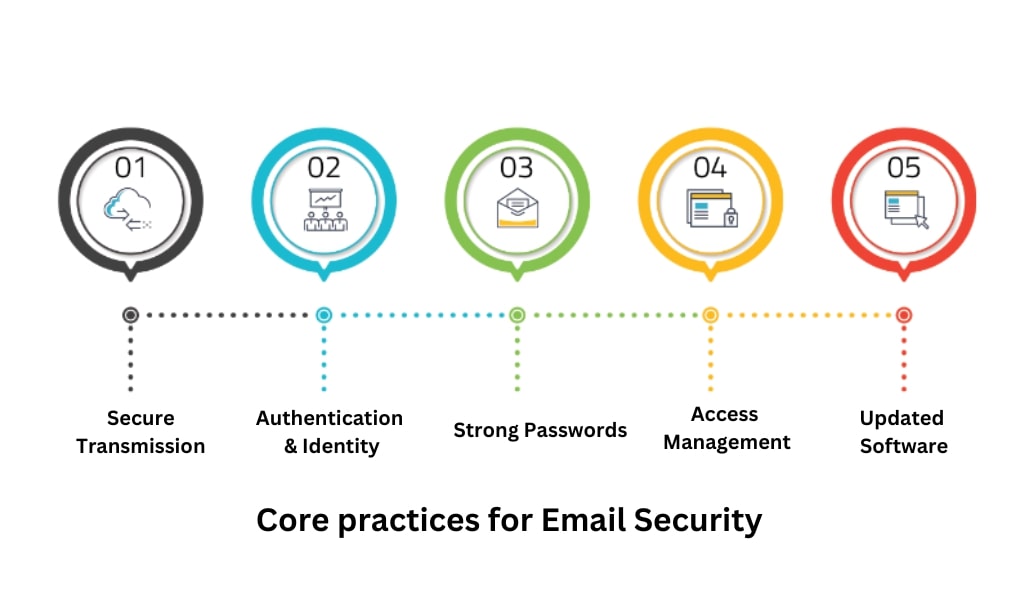
- Secure Transmission - Leading email providers offer TLS/SSL encryption to prevent man-in-the-middle attacks during transit. Using a secure VPN connection provides added protection when accessing email remotely.
- Authentication & Identity - SPF, DKIM, and DMARC authentication validate senders by verifying domain ownership and routing. This prevents spammers from spoofing your domain and improves deliverability.
- Strong Passwords - Require complex passwords, multi factor authentication, and frequent changes to protect accounts. Reusing passwords across accounts leads to wider breaches.
- Access Management - Limit account access to only necessary personnel. Automatically disable inactive accounts after a period of inactivity to reduce risks.
- Updated Software - Keep email infrastructure patched by promptly installing security updates. Follow vendor advisories relating to your email platforms. Outdated software contains exploitable vulnerabilities.
Achieving Optimal Email Security

- Conduct external simulated phishing attacks to identify and address spear phishing vulnerabilities before criminals exploit them. Log all of the simulation data in a risk register for further analysis.
- Implement employee security training to establish secure email handling practices relating to phishing avoidance, authentication, data handling, and more.
- Deploy outbound email filters that inspect all communications for security lapses like sensitive data disclosure, malicious content, or blacklisted destinations.
- Perform compliance audits periodically to verify adherence to privacy laws and regulations when handling customer data via email campaigns.
- Clean email lists regularly by scrubbing bounced addresses and providing an easy opt-out process. This improves deliverability and ensures current subscriber consent.
- Develop an incident response plan that prepares teams to rapidly detect, analyze, contain, and recover from an email-borne attack to minimize damage.
- Test backups and ensure versioning is enabled so compromised data can be restored to an uncompromised state if needed.
- Develop an incident response plan that prepares teams to rapidly detect, analyze, contain, and recover from an email-borne attack to minimize damage.
- Test backups and ensure versioning is enabled so compromised data can be restored to an uncompromised state if needed.
Expanding Your Email Security Perspective

- Building a Security Culture - Foster a workplace culture that ingrains security as a collective responsibility among employees. Provide ongoing training and encourage secure email handling behaviors. Empower employees to proactively identify vulnerabilities and report them. Strengthen human defenses in parallel with technical defenses.
- Collaborating Across Teams - Break down silos by facilitating coordination between departments like marketing, tech, HR, PR, and cybersecurity. Improve visibility by integrating email security insights across groups. Unify efforts toward protecting the organization's overall security posture.
- Prioritizing Customer Trust - Make security and privacy a cornerstone of your customer value proposition. Educate subscribers on threats and provide tips for securely handling emails. Transparency about your security provisions and privacy practices helps build subscriber trust and protect your brand reputation.
- Adopting a Mindset of Constant Vigilance - Treat security as an ongoing discipline rather than a one-time fix. Monitor threat intelligence for new risks. Continuously validate that controls are working via audits and testing. Maintain agility to implement new protections as the threat landscape evolves.
- Securing the Human Attack Surface - People are often the weakest link in security. Prioritize training that builds security awareness and skills for protecting accounts, avoiding phishing scams, reporting incidents, and more. Promote a culture where employees take ownership of security.
Comparing On-Premise vs Cloud-Based Email Security

On-Premise Security
- Total control over hardware and software
- Customization to your unique needs
- Avoid reliance on external providers
- Higher upfront costs for servers and infrastructure
- The burden of manual updates and maintenance
- Limited scalability
Cloud-Based Security
- Lower startup costs by eliminating on-site hardware
- Automatic updates and maintenance
- Scales easily as your needs change
- Access to vast threat intelligence
- Dependency on a third-party provider
- Potential latency from external network traffic
- Limited control and customization
Actionable Tips for Strengthening Your Email Security Posture

- Institute mandatory cybersecurity and phishing prevention training for all employees to build security awareness regarding email handling. Require annual renewal of training.
- Develop security key performance indicators (KPIs) to monitor metrics like phishing click rates, spam complaints, authentication failures, etc. Use insights to strengthen defenses.
- Implement a Secure Email Gateway solution featuring anti-spam, anti-phishing, and anti-malware capabilities powered by artificial intelligence.
- Conduct email penetration testing to proactively identify vulnerabilities before criminals can find them. Address security gaps.
- Leverage threat intelligence feeds to stay updated on emerging threats, new adversary TTPs, malware campaigns, and high-risk indicators of compromise.
- Enforce privileged access management policies providing heightened oversight and auditing of administrator-level email account access.
Email Security FAQs
Conclusion
By taking a big-picture view that integrates technical defenses with cultural and organizational best practices, marketers can continue driving business success while upholding the privacy and trust of subscribers. With proactive vigilance and collective responsibility, the power of email marketing can be harnessed securely.

Mirza Silajdzic | Tech Journalist
LinkedIn: https://www.linkedin.com/in/mirzasilajdzic/
Recent Posts
Why Finding a CEO’s Email Is Harder Than You Think
Discover how to find a CEO's email address, why most common search methods don't work, and which too ...
B2B Email Marketing Automation Workflows (By Use Case)
Explore the best Findymail alternatives in 2026. Compare the features, pricing, reviews, and why Cle ...
How to Implement Gmail & Yahoo Authentication (2026)
Step-by-step guide to implementing Gmail and Yahoo authentication requirements in 2026. Explore how ...
Why Your Emails Hit Gmail's Promotions Tab (and How to Fix It)
Explore why emails land in Gmail’s Promotions tab and how to fix it. Learn proven tips to move emai ...
WPForms Spam Protection: Features, Limitations & Alternatives
Explore how WPForms spam protection works, its limitations, and the best way to prevent fake, dispos ...
Clearout's
Form Guard
Validate email, phone & name on any forms!
- Real signups only
- Verified emails
- Valid phone numbers
- No fake names
- Cleaner CRM
- No devs needed
Email Verification, Email Finding Form Guard & Prospecting Service
Expand Your Reach By Finding & Verifying Ideal Prospects.


